Integrated solutions are your best bet!
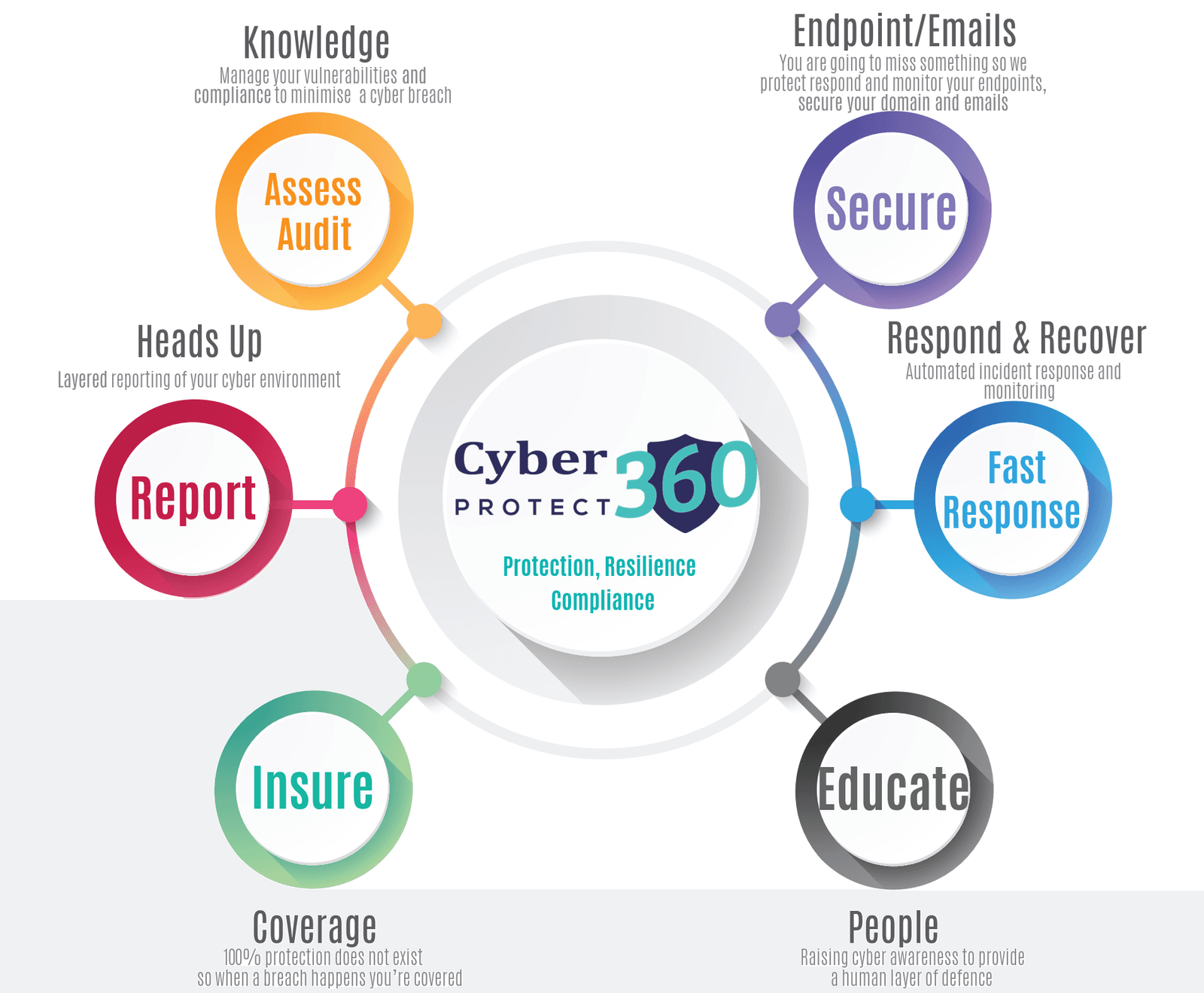
Repeated cyber breaches highlight the urgent need to enhance data management and cybersecurity. Growing threats pose serious operational and financial risks to businesses. National and economic security rely on robust critical infrastructure. To build strong cyber defences, focus on Assessment, Endpoint protection, Education, and Insurance.

seconds there is a hack

records in average data breach

percent of malware is from Emails

dollars SME's lost by ransomware
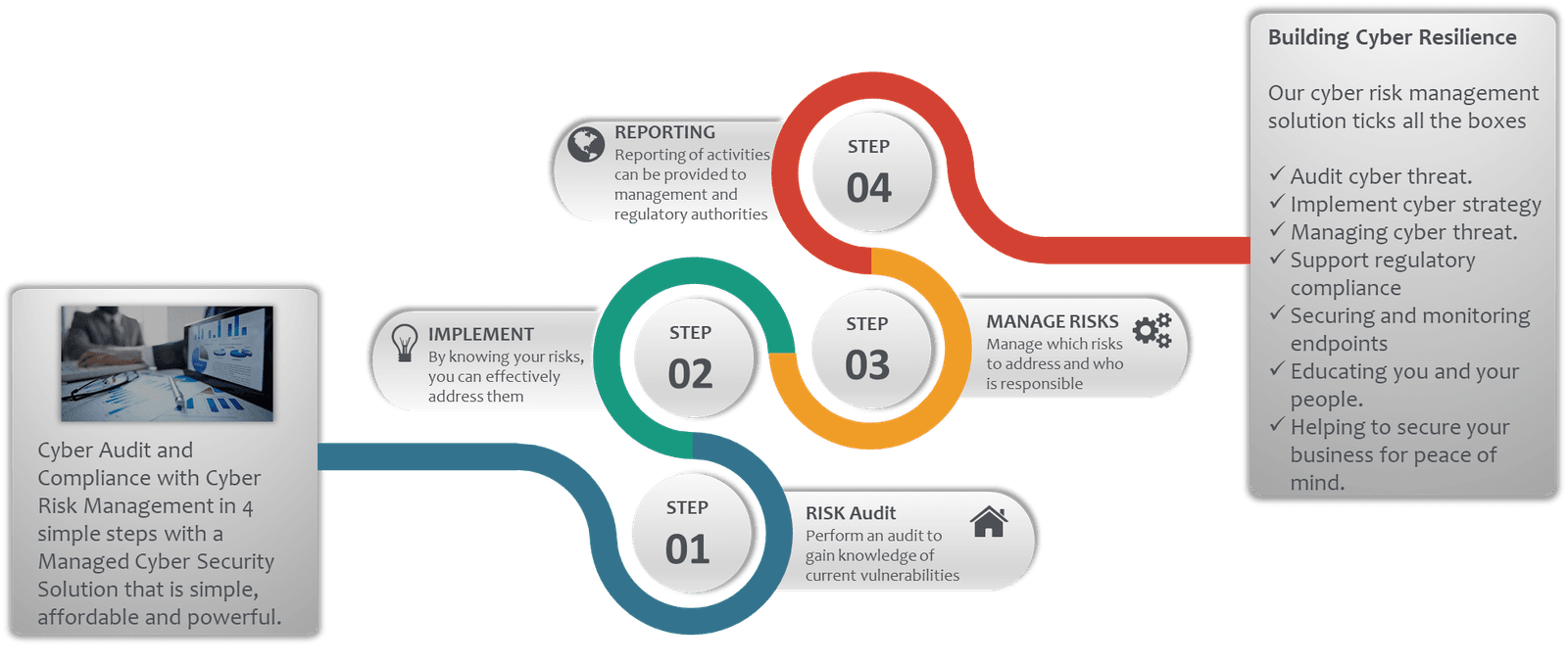
CyberProtect 360: Simple to implement
CyberProtect 360: Multi-layered cyber defence
Cyber Audit
You cannot defend against vulnerabilities you don't know about
Through a holistic cyber audit, an organisation can confidentially determine where improvements are required to strengthen cyber defenses. The audit platform includes recommendations, implementation and compliance management, steps to follow and templates, example policies and procedures to support a poorly resourced sector.
Elements of DP360 include
- Identify your vulnerabilities.
- Address and manage exposures with workflow, including task assignment.
- Historical records.
- Reporting.
- Third party exposure.
- Comprehensive recommendations.
- Insurance requirements.
- Compliance management with workflow.
- Human weaknesses.

Endpoint Protection
The most vulnerable component needs layered protection
CyberProtect 360 Endpoint Protection offers a solution that includes endpoint systems protection, incident response and basic monitoring in a single cohesive security package. The solution to provide endpoint (PCs, Laptops etc.) protection includes at a minimum; .
- Real-time malware protection.
- Vulnerability scanning.
- Enhanced EDR solutions.
- Exploit prevention.
- Protection from Zero day threats.
- Monitoring & reporting.
- Layered proactive defence.

Cyber Education
Failing to educate staff cyber threats will leave SMEs vulnerable.
Failing to educate staff on hacking and cyber threats will leave SMEs vulnerable to simple and mostly avoidable threats. It follows that over a third of cyber claims in 2016 may have been avoided if cyber education and training was put in place for staff. CyberProtect 360 has an education platform that delivers training in 10-15-minute bite-sized modules, these modules raise the level of cyber awareness of staff and support the development of another layer of cyber defence.
Cyber and Data insurance
There is no 100% defence against cyber-attack
It is clear there is no 100% defence against cyber-attack. As part of a holistic business cyber mitigation strategy, a bespoke cyber insurance policy will help to offset the high costs of providing incident response services and associated costs relating to a cyber breach event.
Domain & Email Protection
Partnering with Trusted Sender – Domain and Email protection & monitoring.
Trusted Sender Network is a subscription software service for the management of email and domain security. The software is based on but not limited to the algorithm that provides the free Trusted Sender Score service.
Here are a few questions worth knowing about
- Almost 50 percent of small businesses have experienced a cyber attack
- More than 70 percent of attacks target small businesses
- As much as 60 percent of hacked small and medium-sized businesses go out of business after six months
- Access to client lists
- Customer credit card information
- Your company's banking details
- Your pricing structure
- Product designs
- Staff and client personal information
- Expansion plans
- Manufacturing processes
- Financial losses from theft of banking information
- Financial losses from disruption of business
- High costs to rid your network of threats
- Damage to your reputation after telling customers their information was compromised
- Perform a risk assessment
- Educate your people with cyber awareness
- Protect your endpoints and data
- Get cyber insurance that is affordable and works for you


